
One year ago, in January 2025, we unleashed the very first beta of Pangolin. To be honest, it was a bit lean and had a few "character-building" bugs - but it quickly struck a chord as the go-to open-source alternative to Cloudflare Tunnels for browser-based access.
Fast forward to today, and Pangolin has grown up. We’ve spent the last year stabilizing the core, expanding the feature set, and watching our community thrive. At the end of 2025, we introduced a major new category: Zero-Trust Private Access. This was our answer to months of requests for VPN-like functionality, turning Pangolin into a true one-stop shop for identity-based remote access - whether you’re using a browser or a direct client connection.
Today, we are thrilled to release Pangolin 1.15.0. This update officially takes Private Access out of beta and introduces some heavy hitters: iOS and Android apps, device fingerprinting, posture tracking, and more.
Developing for mobile is a journey through the seven circles of... well, let’s just call it "challenging." Beyond the technical hurdles, there’s the arduous dance with Apple and Google to get through the App Store gates.
After weeks of refreshing our developer dashboards, the wait is over. You can now take your zero-trust network on the road:
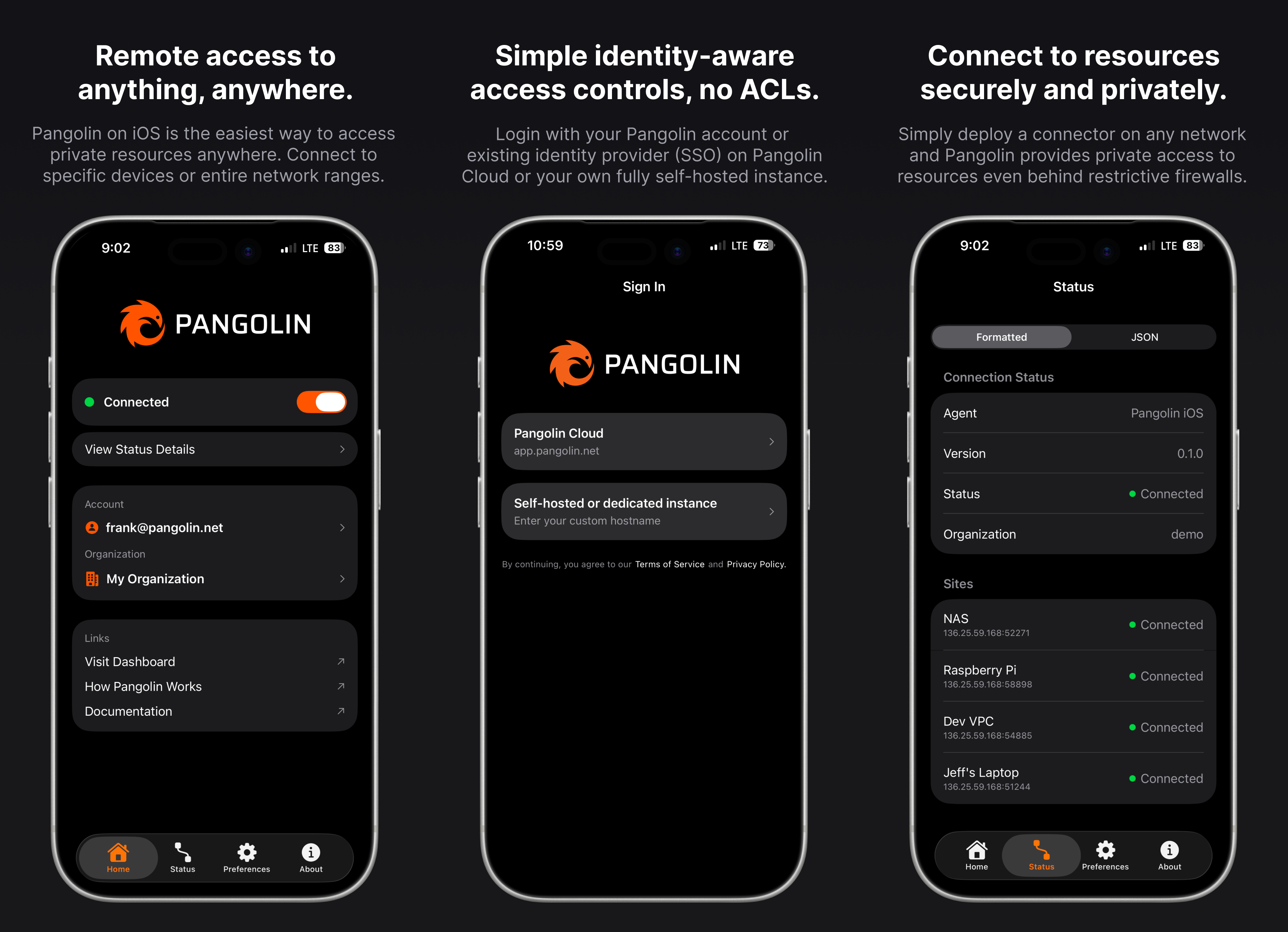
Long-time users likely remember Olm, our Go-based client (named after the small, cave-dwelling salamander). Olm is the workhorse under the hood, handling everything from holepunching and NAT traversal to websocket enforcement.
We architected Olm to be as headless and portable as possible, which allowed us to use it as the "brain" for all of our clients across Mac, Windows, Linux, and iOS and Android. In addition to the Olm core, now each client can collect specific device data to help you secure your perimeter.
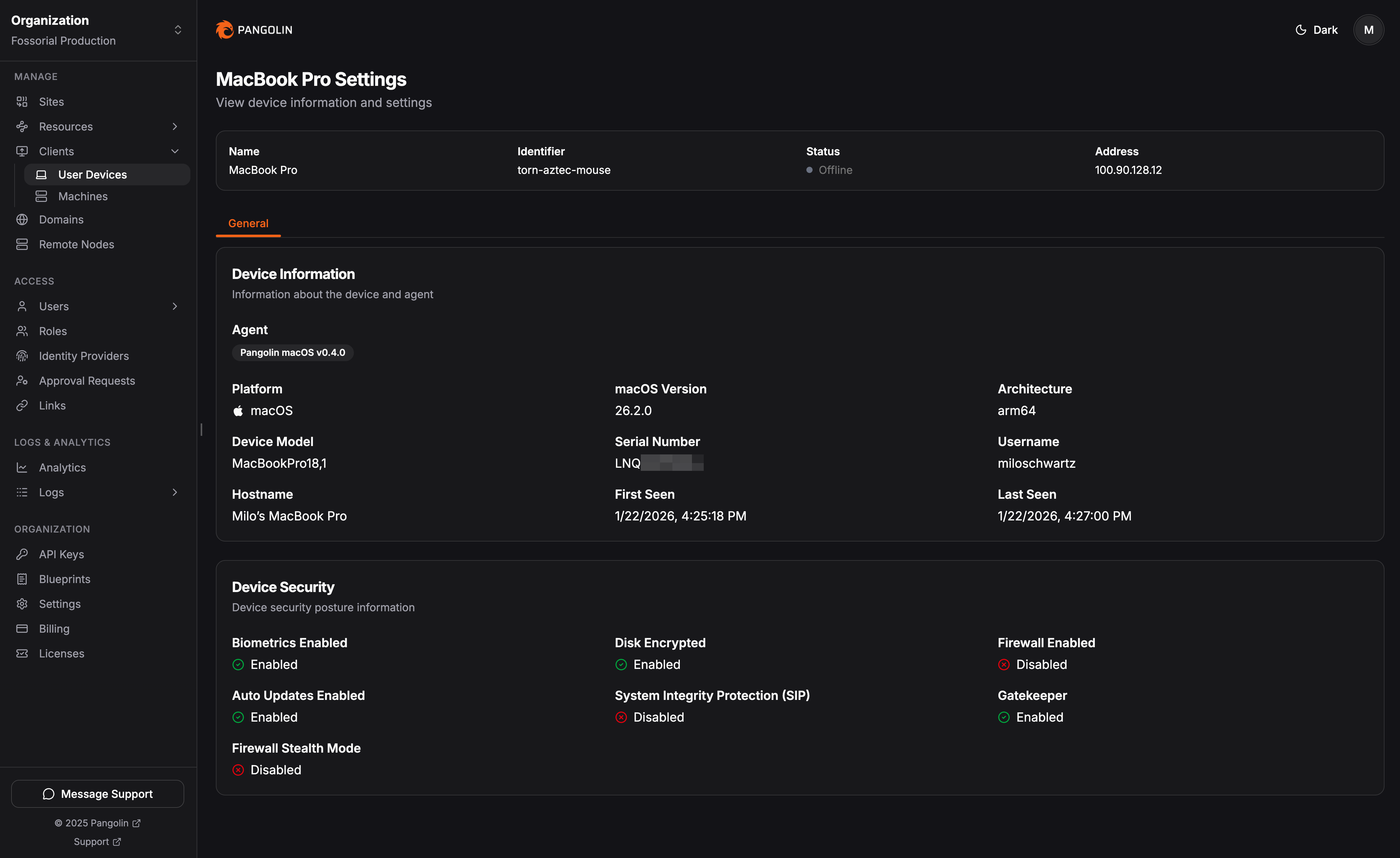
What is fingerprinting? It’s like a digital ID card for your hardware. We collect identifying info like serial numbers, OS versions, and hostnames. This helps admins distinguish between "Bob's Work Laptop" and "Bob's 4th Replacement Laptop," and it ensures that if you block a device, it stays blocked, even if the user tries to wipe their credentials.
What are posture checks? Fingerprinting tells us who the device is; posture checks tell us if the device is healthy. We look for security vitals like:
You can dive into the details in our docs.
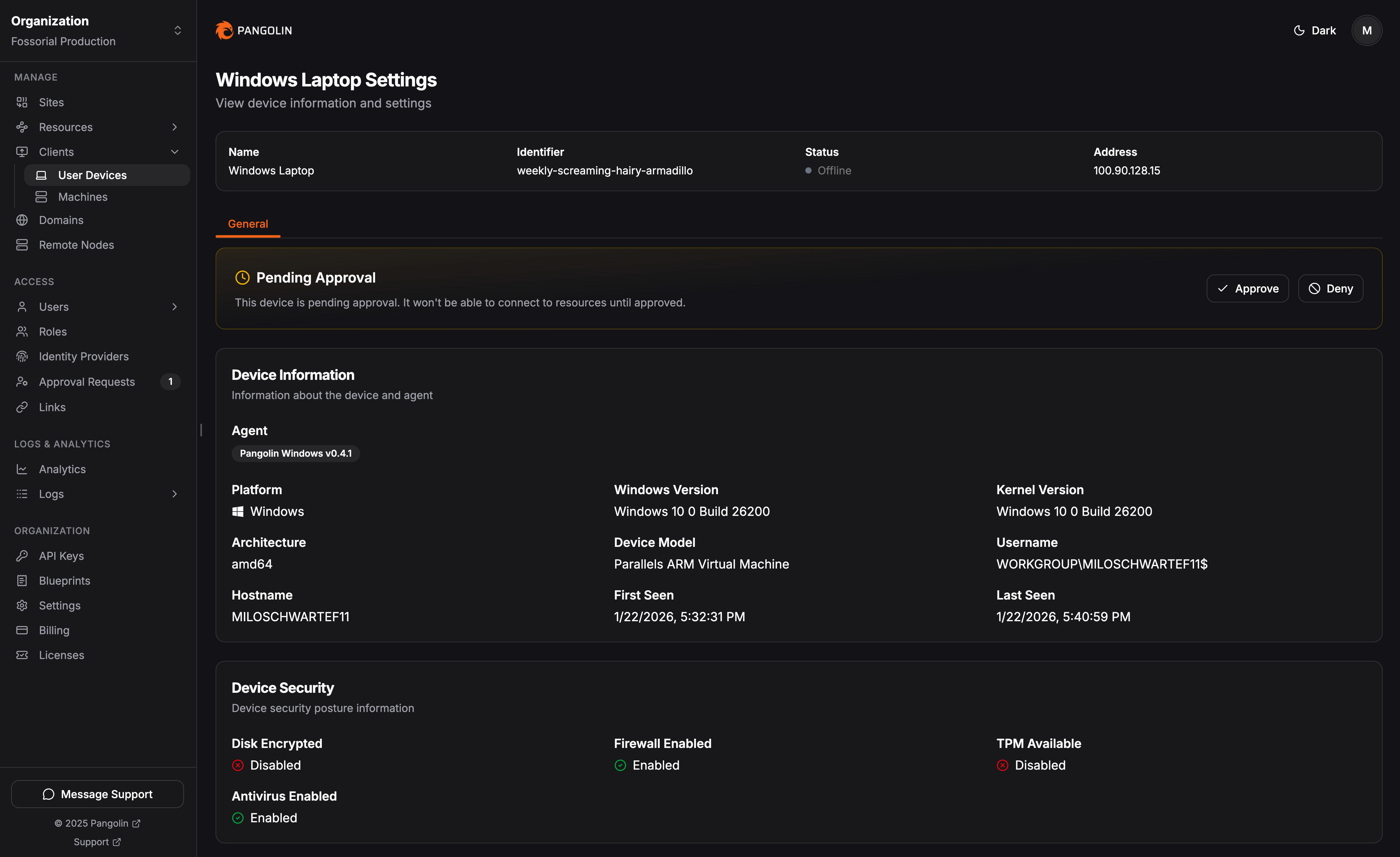
Pangolin Private Access is built on zero-trust principles: admins explicitly define which users and roles can access specific hosts and network ranges. However, until now, those principles primarily applied to resources. By default, a user could connect any number of devices as long as they could log in with an approved account. With version 1.15, we are extending zero-trust to the hardware layer by introducing Device Approvals.
When enabled on a user’s role, Pangolin shifts to a "deny by default" stance for new hardware. Even with valid credentials, a new device is entirely blocked until an admin decisively approves the connection. This works hand-in-hand with our new device posture and fingerprinting features, allowing admins to verify that a device is trusted and secure before letting it through the door.
You can manage this on a per-role basis within the Pangolin dashboard. We’ve added an Approvals Feed to the sidebar where you can see a running log of pending requests. Admins can use this feed to quickly review device details and either approve or deny access, ensuring that only authorized hardware can touch your network.

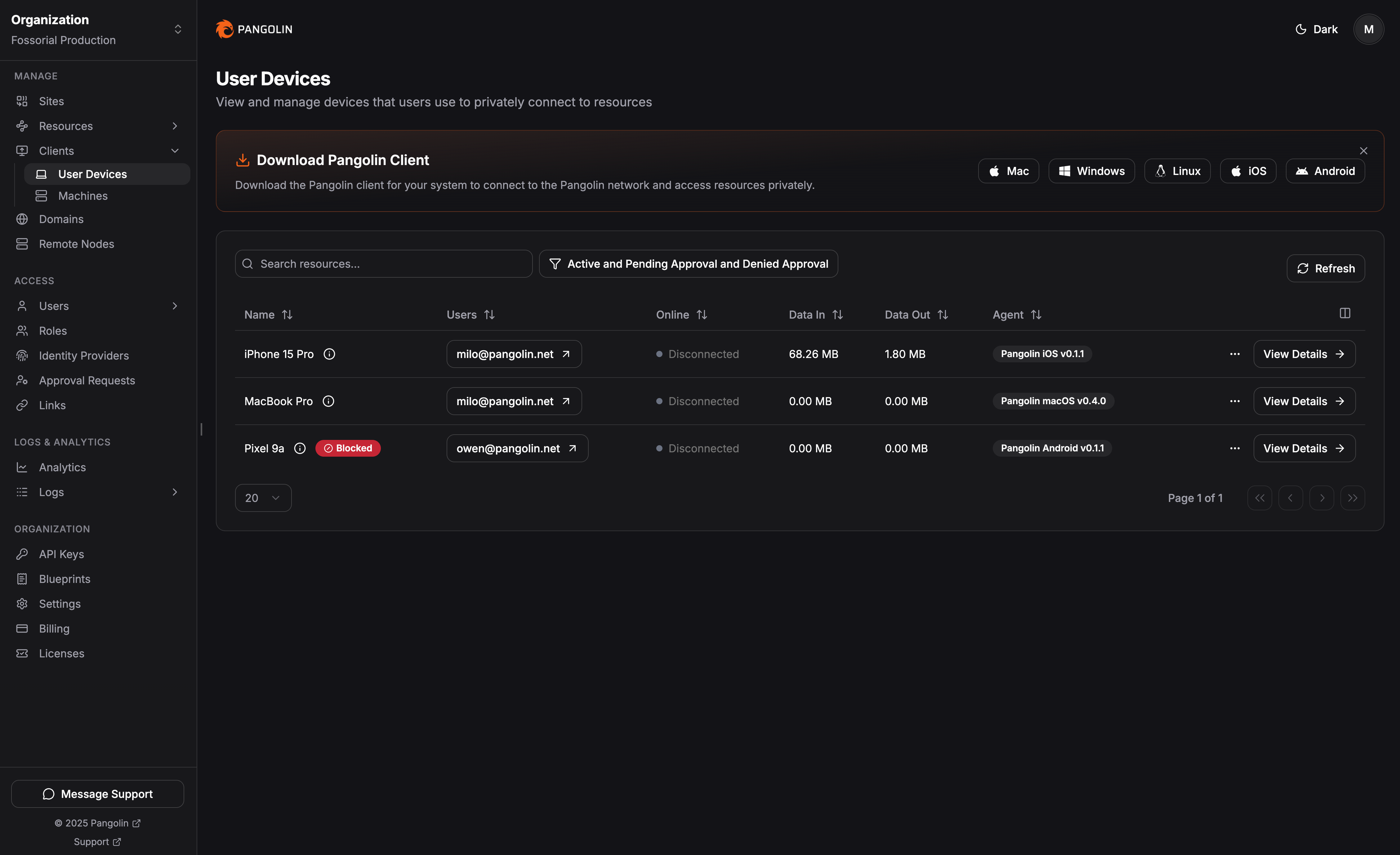
Have a device that’s gone rogue or been lost? You can now officially Block it via the Action Menu (three dots). This moves the device to a restricted list and kills its access immediately.
You’ll also notice you can’t "delete" a device; you can only Archive it.
Why no delete button? For security, Pangolin keeps a permanent record of every device that has touched your resources. If you could delete a device entirely, an admin's "Block" rule would vanish with it. Archiving keeps your UI clean of old or duplicate devices while keeping your security audit trail intact.
As demonstrated by dropping the beta tag from the private access features in Pangolin, we worked hard on stability and performance for all of Pangolin’s clients and private connectivity features.
We are incredibly proud of 1.15.0. Between the mobile apps and the new zero-trust controls, Pangolin is more flexible and secure than ever.
You can jump in today with a free account on Pangolin Cloud. or stick to your roots and self-host the Open Source Community or Enterprise Editions.
Thanks for being part of the journey!